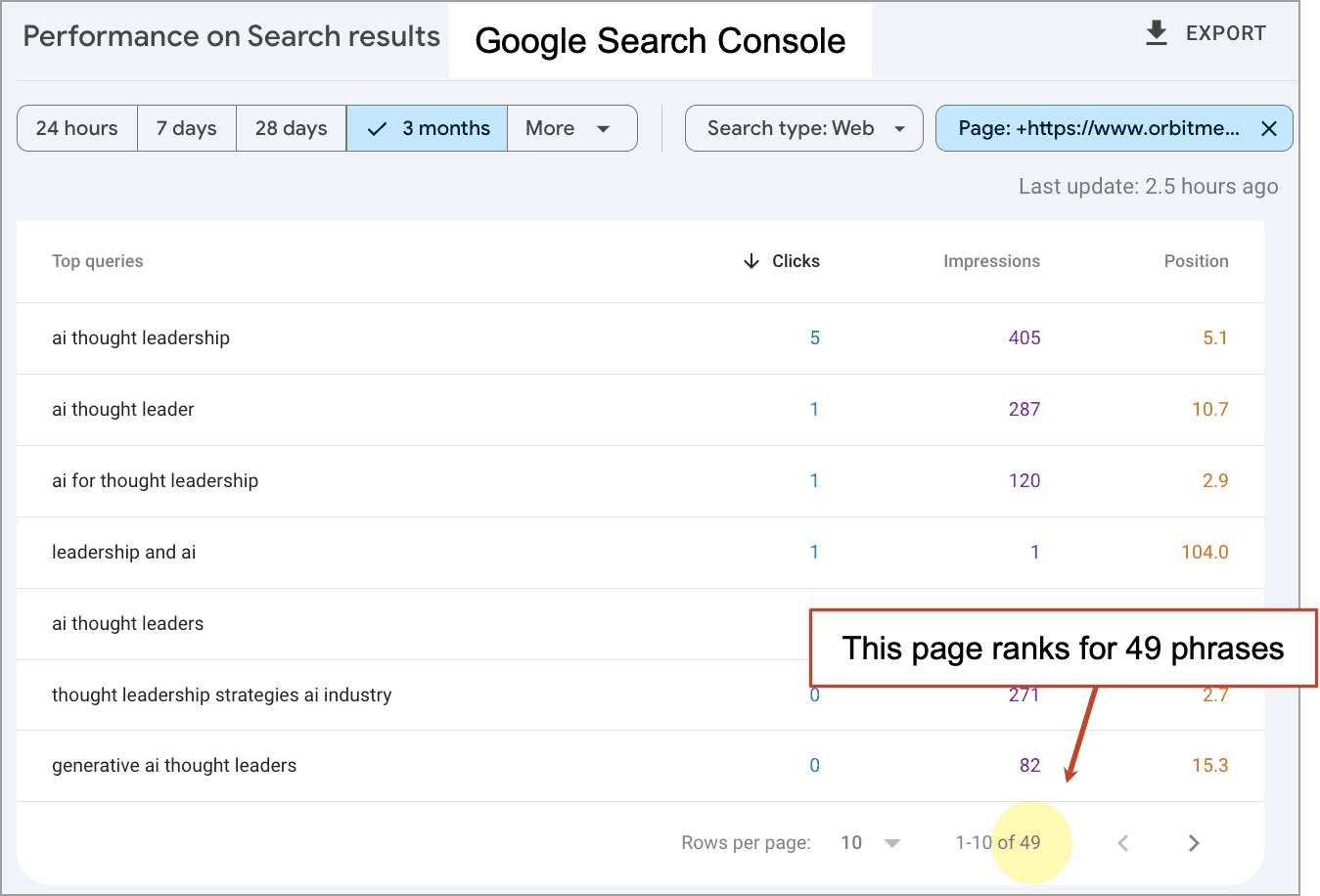
FBI warning: What is Medusa ransomware and how can you protect yourself from getting hacked?
In the past week, law enforcement agencies including the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have issued a warning about the ongoing threat of Medusa ransomware. Here’s what you need to know about the threat and how you can protect yourself. What is Medusa ransomware? Ransomware is a type of software that is designed to compromise your information, allowing hackers to steal it. Once these bad actors have your data, they then contact you (or the software contacts you on their behalf), and they inform you that unless you pay a ransom, your data will either be deleted, sold to the highest bidder, or released publicly for all to see. Medusa ransomware is a specific type of ransomware that is currently making the rounds. According to a cybersecurity advisory published by the Cybersecurity and Infrastructure Security Agency (CISA), Medusa ransomware “is a ransomware-as-a-service (RaaS)” that has been going around since at least June 2021. The advisory states that Medusa relies on “a double extortion model”—that encrypts the data on a victim’s hard drive so they can’t access it, as well as threatens to decrypt the data and sell it to third parties or release it publicly. Users must pay a ransom in order to gain access to their encrypted files again and/or in order to ensure that the files are not disseminated to additional parties. Ransom payments can range anywhere between $100 to $1 million. The CISA says that as of February 2025, Medusa has impacted “over 300 victims from a variety of critical infrastructure sectors,” which include medical, education, legal, insurance, technology, and manufacturing. How can I protect myself and my company from Medusa? The advisory posted on the CISA’s website states that Medusa is primarily spread through phishing campaigns to steal victims’ credentials. The ransomware can also infiltrate a system through unpatched software vulnerabilities. With that in mind, the notice states that there are several steps an individual and organization can take to mitigate threats from Medusa. These include: Using long passwords on accounts. Implementing multifactor authentication (also known as MFA or 2FA) on accounts. Keeping software and operating systems on all devices up to date. Use VPNs to protect your traffic. Have multiple copies of sensitive data backed up on more than just one device. Finally, it’s always a good idea to practice common sense measures that help reduce your vulnerability to phishing attempts. This includes never clicking on a link that is emailed or texted to you if you don’t recognize the sender. Likewise, never open attachments you receive from an unknown sender. And even when a sender appears legitimate, it is always best to contact them via another channel to ensure that they, indeed, were the one who sent you a link or attachment. A common phishing tactic bad actors use is to send emails to victims that appear to be from valid or known email addresses—but when you look closely at them, you’ll see that a character or two might have been changed. For example, an “I” in an email address might have been changed to a “1”). At first glance, the email looks legitimate, but the change is a giveaway that someone is trying to misrepresent who they actually are. The CISA maintains a webpage with myriad tips detailing how to further protect yourself from ransomware.

In the past week, law enforcement agencies including the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have issued a warning about the ongoing threat of Medusa ransomware. Here’s what you need to know about the threat and how you can protect yourself.
What is Medusa ransomware?
Ransomware is a type of software that is designed to compromise your information, allowing hackers to steal it. Once these bad actors have your data, they then contact you (or the software contacts you on their behalf), and they inform you that unless you pay a ransom, your data will either be deleted, sold to the highest bidder, or released publicly for all to see.
Medusa ransomware is a specific type of ransomware that is currently making the rounds. According to a cybersecurity advisory published by the Cybersecurity and Infrastructure Security Agency (CISA), Medusa ransomware “is a ransomware-as-a-service (RaaS)” that has been going around since at least June 2021.
The advisory states that Medusa relies on “a double extortion model”—that encrypts the data on a victim’s hard drive so they can’t access it, as well as threatens to decrypt the data and sell it to third parties or release it publicly.
Users must pay a ransom in order to gain access to their encrypted files again and/or in order to ensure that the files are not disseminated to additional parties. Ransom payments can range anywhere between $100 to $1 million.
The CISA says that as of February 2025, Medusa has impacted “over 300 victims from a variety of critical infrastructure sectors,” which include medical, education, legal, insurance, technology, and manufacturing.
How can I protect myself and my company from Medusa?
The advisory posted on the CISA’s website states that Medusa is primarily spread through phishing campaigns to steal victims’ credentials. The ransomware can also infiltrate a system through unpatched software vulnerabilities.
With that in mind, the notice states that there are several steps an individual and organization can take to mitigate threats from Medusa. These include:
- Using long passwords on accounts.
- Implementing multifactor authentication (also known as MFA or 2FA) on accounts.
- Keeping software and operating systems on all devices up to date.
- Use VPNs to protect your traffic.
- Have multiple copies of sensitive data backed up on more than just one device.
Finally, it’s always a good idea to practice common sense measures that help reduce your vulnerability to phishing attempts. This includes never clicking on a link that is emailed or texted to you if you don’t recognize the sender. Likewise, never open attachments you receive from an unknown sender.
And even when a sender appears legitimate, it is always best to contact them via another channel to ensure that they, indeed, were the one who sent you a link or attachment. A common phishing tactic bad actors use is to send emails to victims that appear to be from valid or known email addresses—but when you look closely at them, you’ll see that a character or two might have been changed.
For example, an “I” in an email address might have been changed to a “1”). At first glance, the email looks legitimate, but the change is a giveaway that someone is trying to misrepresent who they actually are.
The CISA maintains a webpage with myriad tips detailing how to further protect yourself from ransomware.






















































































![Building A Digital PR Strategy: 10 Essential Steps for Beginners [With Examples]](https://buzzsumo.com/wp-content/uploads/2023/09/Building-A-Digital-PR-Strategy-10-Essential-Steps-for-Beginners-With-Examples-bblog-masthead.jpg)




![How Human Behavior Impacts Your Marketing Strategy [Video]](https://contentmarketinginstitute.com/wp-content/uploads/2025/03/human-behavior-impacts-marketing-strategy-cover-600x330.png?#)


![How to Make a Content Calendar You’ll Actually Use [Templates Included]](https://marketinginsidergroup.com/wp-content/uploads/2022/06/content-calendar-templates-2025-300x169.jpg?#)
![How to Use GA4 to Track Social Media Traffic: 6 Questions, Answers and Insights [VIDEO]](https://www.orbitmedia.com/wp-content/uploads/2023/06/ab-testing.png)